The Unseen Threat in Open Source Software: A Case Study of CVE-2024-3094 (The XZ Utils Backdoor)
Last week, the tech community was alerted to a critical vulnerability in XZ Utils, a widely-used open source compression tool in Linux systems. This backdoor, embedded with sophisticated engineering and social manipulation, nearly infiltrated major Linux distributions like Debian and Red Hat. The detection of this threat, thanks to the vigilance of a Microsoft engineer, Andres Freund, prevented a potential cybersecurity disaster.
Understanding XZ Utils and the Threat
XZ Utils is integral for data compression across various Unix-like operating systems. The discovered backdoor altered the software’s functions, specifically targeting SSH connections. This cleverly designed backdoor allowed execution of arbitrary code, posing serious security risks.
Inception and Detection of the Backdoor
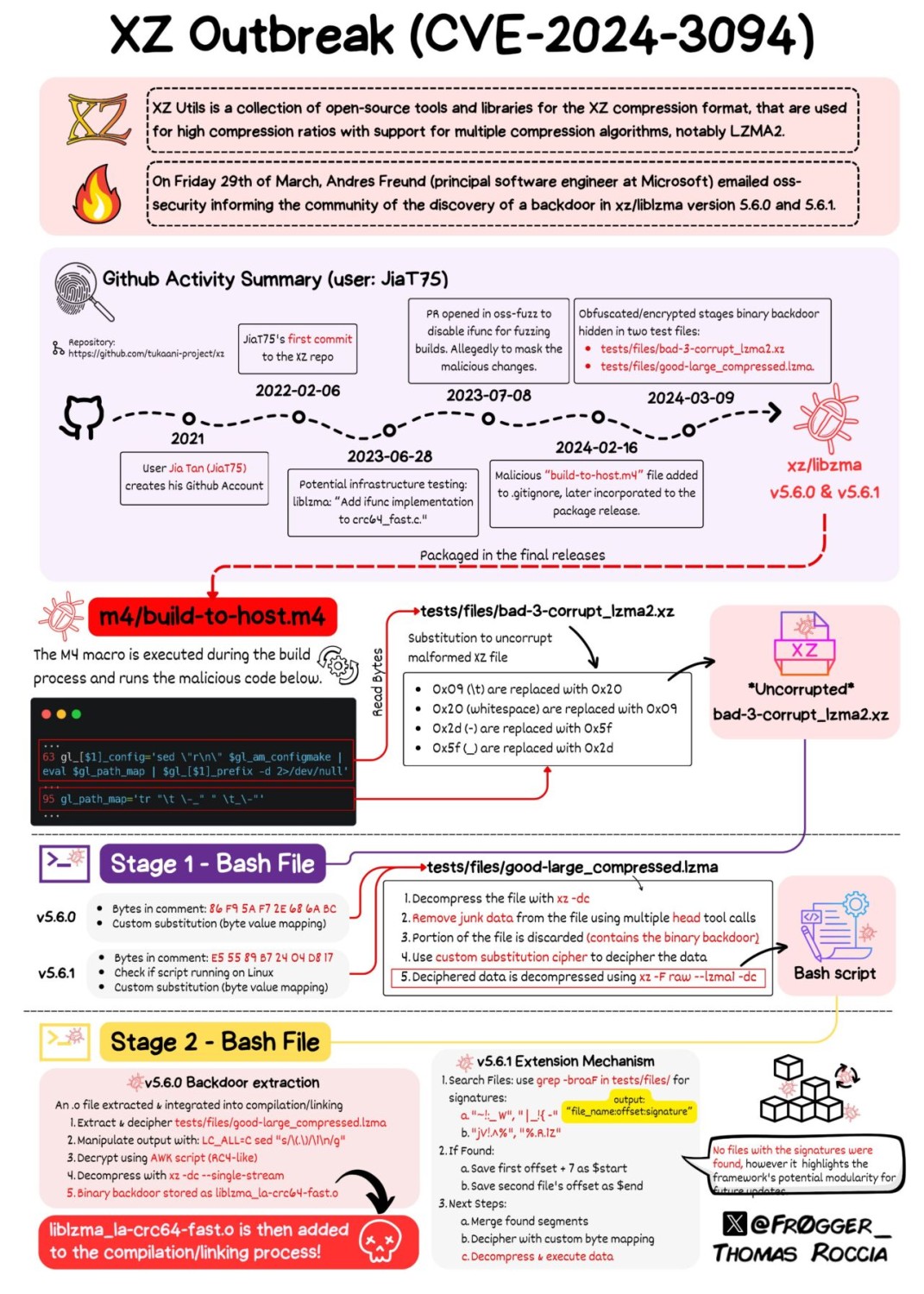
This backdoor’s inception, traced back to a contributor known as JiaT75, highlights a calculated, long-term strategy to infiltrate the open-source project. It’s a chilling reminder of the vulnerabilities within supply chains and open-source software.
Mitigating the Risks
To address such hidden threats, businesses need a robust cybersecurity approach. Standard practices like complex passwords and 2FA are not enough. Companies should consider advanced solutions like Intrusion Detection Systems, stringent firewall configurations, vigilant software audits, and the use of a VPN and/or other solutions to restrict access to your systems . At Acuuis IT, we emphasize the importance of these proactive measures in safeguarding your digital infrastructure.
Navigating the Future of Cybersecurity
The CVE-2024-3094 case is a testament to the ever-evolving nature of cyber threats. As an IT leader, I stress the importance of staying ahead through constant vigilance and updated cybersecurity strategies. Let’s learn and prepare for a more secure digital future.
So what now?
No business, regardless of size, is immune to cyber attacks. The CVE-2024-3094 incident exemplifies how even following best practices can leave companies exposed to complex threats, including those potentially orchestrated by foreign governments. These attacks are often automated, indiscriminately targeting vulnerable systems. It’s crucial for every business to establish a robust cybersecurity and disaster recovery plan.
As a Managed IT services and Cybersecurity provider based in Myrtle Beach, SC, Acuuis IT is dedicated to protecting businesses from such threats. Contact us at [email protected] or call 843-620-6048 for a complimentary Cybersecurity Audit, and ensure your business is fortified against the ever-evolving landscape of cyber threats.



